None
<p></p><center data-preserve-html-node="true">Author, Creator & Presenter: Dr. Johanna Sepúlveda PhD, Senior Expert and Technical Domain Manager for Quantum and Quantum-Secure Technologies, Airbus Defence and Space
<p></p><center data-preserve-html-node="true"><iframe allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" referrerpolicy="strict-origin-when-cross-origin" allowfullscreen="" src="https://www.youtube-nocookie.com/embed/kFqPzXs8Cj8?si=AK89JqMvzFbivN9C" width="560" frameborder="0" data-preserve-html-node="true" title="YouTube video player" height="315"></iframe>
<p>Our thanks to the <strong><a href="https://www.ndss-symposium.org/">Network and Distributed System Security (NDSS) Symposium</a></strong> for publishing their Creators, Authors and Presenter’s superb <strong><a href="https://www.youtube.com/@NDSSSymposium">NDSS Symposium 2025 Conference</a></strong> content on the <strong><a href="https://www.ndss-symposium.org/">organization’s’</a></strong> <strong><a href="https://youtube.com/@ndsssymposium?si=lLtn9sVVEwmZ8J9h">YouTube</a></strong> channel. </p><div class="code-block code-block-12 ai-track" data-ai="WzEyLCIiLCJCbG9jayAxMiIsIiIsMV0=" style="margin: 8px 0; clear: both;">
<style>
.ai-rotate {position: relative;}
.ai-rotate-hidden {visibility: hidden;}
.ai-rotate-hidden-2 {position: absolute; top: 0; left: 0; width: 100%; height: 100%;}
.ai-list-data, .ai-ip-data, .ai-filter-check, .ai-fallback, .ai-list-block, .ai-list-block-ip, .ai-list-block-filter {visibility: hidden; position: absolute; width: 50%; height: 1px; top: -1000px; z-index: -9999; margin: 0px!important;}
.ai-list-data, .ai-ip-data, .ai-filter-check, .ai-fallback {min-width: 1px;}
</style>
<div class="ai-rotate ai-unprocessed ai-timed-rotation ai-12-1" data-info="WyIxMi0xIiwxXQ==" style="position: relative;">
<div class="ai-rotate-option" style="visibility: hidden;" data-index="1" data-name="VGVjaHN0cm9uZyBHYW5nIFlvdXR1YmU=" data-time="MTA=">
<div class="custom-ad">
<div style="margin: auto; text-align: center;"><a href="https://youtu.be/Fojn5NFwaw8" target="_blank"><img src="https://securityboulevard.com/wp-content/uploads/2024/12/Techstrong-Gang-Youtube-PodcastV2-770.png" alt="Techstrong Gang Youtube"></a></div>
<div class="clear-custom-ad"></div>
</div></div>
</div>
</div>
<p></p></center></center><p><a href="https://www.infosecurity.us/blog/2025/10/11/ndss-2025-keynote-1-quantum-security-unleashed-a-new-era-for-secure-communications-and-systems">Permalink</a></p><p>
</p><div class="spu-placeholder" style="display:none"></div><div class="addtoany_share_save_container addtoany_content addtoany_content_bottom"><div class="a2a_kit a2a_kit_size_20 addtoany_list" data-a2a-url="https://securityboulevard.com/2025/10/ndss-2025-keynote-1-quantum-security-unleashed-a-new-era-for-secure-communications-and-systems/" data-a2a-title="NDSS 2025 – Keynote 1: Quantum Security Unleashed: A New Era for Secure Communications and Systems"><a class="a2a_button_twitter" href="https://www.addtoany.com/add_to/twitter?linkurl=https%3A%2F%2Fsecurityboulevard.com%2F2025%2F10%2Fndss-2025-keynote-1-quantum-security-unleashed-a-new-era-for-secure-communications-and-systems%2F&linkname=NDSS%202025%20%E2%80%93%20Keynote%201%3A%20Quantum%20Security%20Unleashed%3A%20A%20New%20Era%20for%20Secure%20Communications%20and%20Systems" title="Twitter" rel="nofollow noopener" target="_blank"></a><a class="a2a_button_linkedin" href="https://www.addtoany.com/add_to/linkedin?linkurl=https%3A%2F%2Fsecurityboulevard.com%2F2025%2F10%2Fndss-2025-keynote-1-quantum-security-unleashed-a-new-era-for-secure-communications-and-systems%2F&linkname=NDSS%202025%20%E2%80%93%20Keynote%201%3A%20Quantum%20Security%20Unleashed%3A%20A%20New%20Era%20for%20Secure%20Communications%20and%20Systems" title="LinkedIn" rel="nofollow noopener" target="_blank"></a><a class="a2a_button_facebook" href="https://www.addtoany.com/add_to/facebook?linkurl=https%3A%2F%2Fsecurityboulevard.com%2F2025%2F10%2Fndss-2025-keynote-1-quantum-security-unleashed-a-new-era-for-secure-communications-and-systems%2F&linkname=NDSS%202025%20%E2%80%93%20Keynote%201%3A%20Quantum%20Security%20Unleashed%3A%20A%20New%20Era%20for%20Secure%20Communications%20and%20Systems" title="Facebook" rel="nofollow noopener" target="_blank"></a><a class="a2a_button_reddit" href="https://www.addtoany.com/add_to/reddit?linkurl=https%3A%2F%2Fsecurityboulevard.com%2F2025%2F10%2Fndss-2025-keynote-1-quantum-security-unleashed-a-new-era-for-secure-communications-and-systems%2F&linkname=NDSS%202025%20%E2%80%93%20Keynote%201%3A%20Quantum%20Security%20Unleashed%3A%20A%20New%20Era%20for%20Secure%20Communications%20and%20Systems" title="Reddit" rel="nofollow noopener" target="_blank"></a><a class="a2a_button_email" href="https://www.addtoany.com/add_to/email?linkurl=https%3A%2F%2Fsecurityboulevard.com%2F2025%2F10%2Fndss-2025-keynote-1-quantum-security-unleashed-a-new-era-for-secure-communications-and-systems%2F&linkname=NDSS%202025%20%E2%80%93%20Keynote%201%3A%20Quantum%20Security%20Unleashed%3A%20A%20New%20Era%20for%20Secure%20Communications%20and%20Systems" title="Email" rel="nofollow noopener" target="_blank"></a><a class="a2a_dd addtoany_share_save addtoany_share" href="https://www.addtoany.com/share"></a></div></div><p class="syndicated-attribution">*** This is a Security Bloggers Network syndicated blog from <a href="https://www.infosecurity.us/">Infosecurity.US</a> authored by <a href="https://securityboulevard.com/author/0/" title="Read other posts by Marc Handelman">Marc Handelman</a>. Read the original post at: <a href="https://www.youtube-nocookie.com/embed/kFqPzXs8Cj8?si=AK89JqMvzFbivN9C">https://www.youtube-nocookie.com/embed/kFqPzXs8Cj8?si=AK89JqMvzFbivN9C</a> </p>
Apple raised bug bounties to $2M for zero-click RCEs, doubling payouts. Since 2020, it’s paid $35M to 800 researchers. Apple doubled its bug bounty rewards, now offering up to $2 million for zero-click remote code execution flaws. Since 2020, the tech giant h…
Apple doubles maximum bug bounty to $2M for zero-click RCEs
Apple doubled its bug bounty rewards, now offering up to $2 million for zero-click remote code execution flaws. Since 2020, the tech giant… [+4180 chars]
Journalists beware.
It appears the Israel-based NSO Groupa notorious peddler of powerfully invasive spywarehas been purchased by an American company. The news was first reported by Israeli outlet Calcalist and confirmed… [+2702 chars]
Prince Harry and Meghan urged parents to stand against social media companies that they said lure children with predatory algorithms designed to exploit their data amid the “explosion of unregulated artificial intelligence.” “Like so many parents, we think co…
Prince Harry and Meghan urged parents to stand against social media companies that they said lure children with predatory algorithms designed to exploit their data amid the explosion of unregulated a… [+6086 chars]
Someone left a cold seltzer can on my $25 thrifted coffee table, which left the above water mark. Luckily I noticed it the next morning and knew of a reversal method, which was mostly likely successful because the damage was fresh. That method? Running an iro…
The Non-Consumer Advocate
<ol><li>Someone left a cold seltzer can on my $25 thrifted coffee table, which left the above water mark. Luckily I noticed it the next morning and knew of a reversal metho… [+1731 chars]
Staking has become one of the most popular ways for crypto holders to earn rewards […]
Staking has become one of the most popular ways for crypto holders to earn rewards while supporting blockchain networks. By committing their assets, users contribute to network security and transacti… [+5626 chars]
The couple announced their foundation's Parents Network would join forces with ParentsTogether.
By JAMES POLLARD, Associated Press
NEW YORK (AP) Prince Harry and Meghan urged parents to stand against social media companies that they said lure children with predatory algorithms designed to expl… [+6320 chars]
NSO Group confirmed to TechCrunch that an unnamed group of American investors has taken “controlling ownership” of the surveillance tech maker.
Israeli spyware maker NSO Group has confirmed to TechCrunch that a U.S. investment group has acquired the company.
NSO spokesperson Oded Hershowitz told TechCrunch on Friday that an American inves… [+3984 chars]
Key takeaways
Former CEO of Google, Eric Schmidt, warned about the security vulnerabilities surrounding AI models this week.
Schmidt did also praise the technology and its potential, saying that it is currently “underhyped.”
“While AI does present securit…
Key takeaways
Former CEO of Google, Eric Schmidt, warned about the security vulnerabilities surrounding AI models this week.Schmidt did also praise the technology and its potential, saying that it i… [+134 chars]
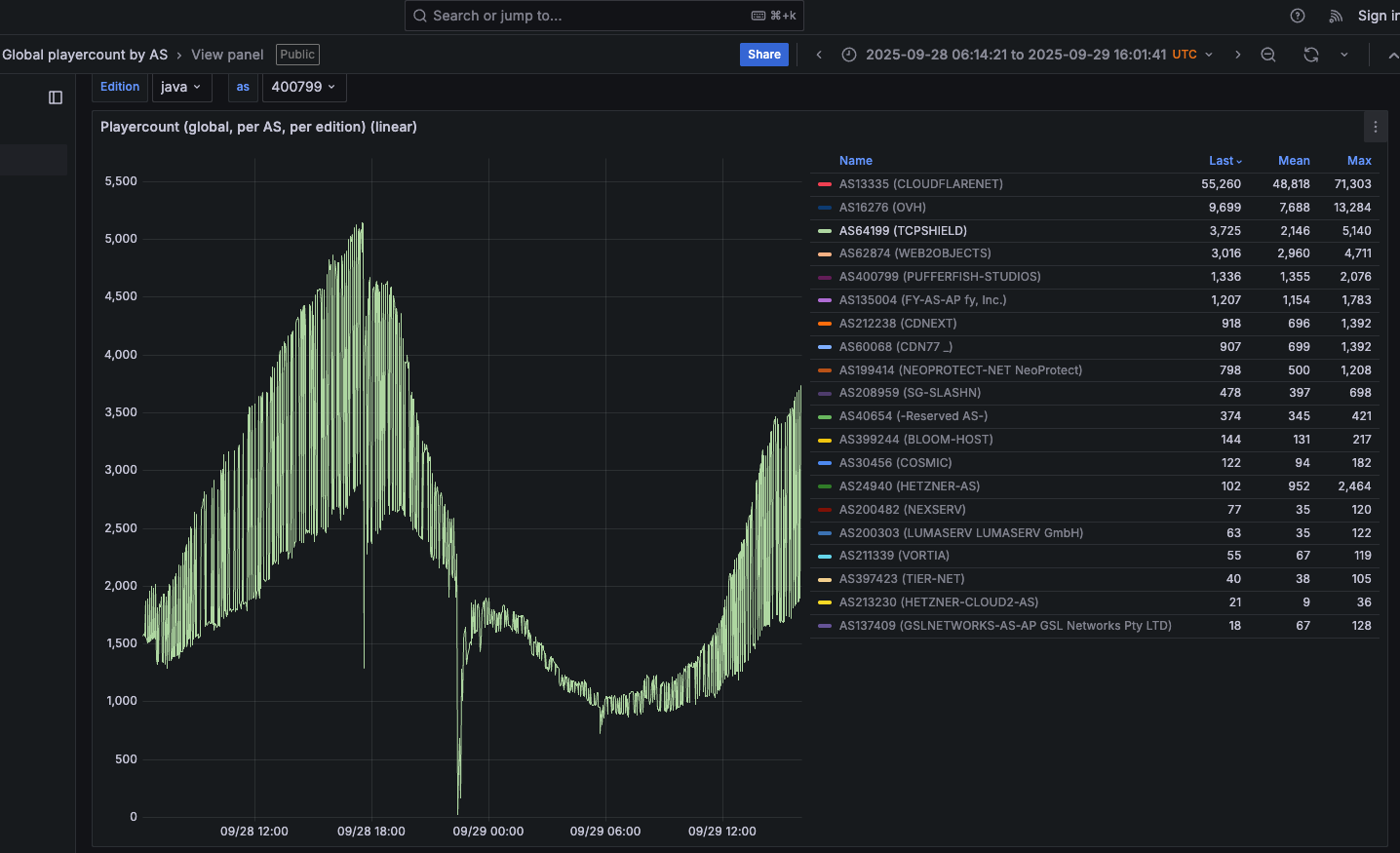
The world's largest and most disruptive botnet is now drawing a majority of its firepower from compromised Internet-of-Things (IoT) devices hosted on U.S. Internet providers like AT&T, Comcast and Verizon, new evidence suggests. Experts say the heavy concentr…
The world’s largest and most disruptive botnet is now drawing a majority of its firepower from compromised Internet-of-Things (IoT) devices hosted on U.S. Internet providers like AT&T, Comcast an… [+14252 chars]
To win big at Texas Hold-Em, a player needs considerable skill, no small amount of luck...and it wouldn't hurt to know what every other player is holding, either. WIRED's Andy Greenberg teams up with casino cheating expert Sal Piacente and hacker/researcher J…
To win big in poker, you need skill, luck,
and it helps if you somehow know the cards
in every other player's hands.
I'm a terrible poker player,
but I teamed up with this casino cheating expert
… [+27304 chars]
A financially-motivated hacking group, tracked by Microsoft as Storm-2657, has so far successfully compromised employee accounts at three U.S. universities to steal their salaries in what campaign experts are deeming "payroll pirate" attacks. The sophisticate…
A financially-motivated hacking group, tracked by Microsoft as Storm-2657, has so far successfully compromised employee accounts at three U.S. universities to steal their salaries in what campaign ex… [+2896 chars]
“There was something greater going on,” the 2012 Tour de France winner said in an interview detailing his cocaine addiction, bankruptcy, and the sexual abuse he suffered as a teenager
Sir Bradley Wiggins has claimed that Team Sky chucked me under a bus concerning the doping allegations levelled against him, the 2012 Tour de France winner insinuating that the resulting scandals wer… [+7636 chars]
Indie game developer and publisher Flatline Studios has confirmed that Into The Grid will be released into Early Access next month. The cyberpunk roguelike deckbuilder game has gone through a quick development, as well as having a free demo out this Summer to…
Posted in: Games, Indie Games, Video Games | Tagged: Flatline Studios, Into The Grid
After having already had a free demo and a few teasers, the game Into The Grid will be coming out in Early Access… [+2891 chars]
The What Happened to This Horror Movie series looks back at director David Gordon Green's 2018 Halloween sequel
The post Halloween (2018) – What Happened to This Horror Movie? appeared first on JoBlo.
The history of the Halloween film franchise is a long and winding one; when you consider the many sequels and reboots the classic John Carpenter original spawned, its hard to think of another movie s… [+10112 chars]
Juniper fixed nearly 220 flaws in Junos OS, Junos Space, and Security Director, including nine critical bugs in Junos Space. Juniper Networks released patches to address nearly 220 vulnerabilities in Junos OS, Junos Space, and Security Director, including nin…
Juniper patched nine critical flaws in Junos Space
Juniper Networks released patches to address nearly 220 vulnerabilities in Junos OS, Junos Space, and Security Director, including nine critical fl… [+1805 chars]
Telcos are collaborating on the deployment and launch of common network APIs in multiple markets across AsiaIndia’s three leading mobile operators are helping …
Mobile network operators in multiple markets across Asia are collaborating on the deployment and launch of common network APIs that can ultimately help to tackle serious problems such as digital frau… [+8207 chars]
Russia-linked actors use AI to craft phishing and malware attacks against entities in Ukraine, says SSSCIP. Russian hackers increasingly use AI in cyberattacks against Ukraine, the country’s State Service for Special Communications and Information Protection …
Ukraine sees surge in AI-Powered cyberattacks by Russia-linked Threat Actors
Russian hackers increasingly use AI in cyberattacks against Ukraine, the country’s State Service for Special Communicatio… [+2955 chars]
Prince Harry and Meghan Markle are urging parents to stand against wealthy social media companies that they said prey upon children with algorithms designed to exploit personal data. To build their movement of families fighting for online safety, the couple a…
NEW YORK (AP) Prince Harry and Meghan Markle urged parents to stand against social media companies that they said prey upon children with exploitative algorithms as the explosion of unregulated artif… [+5370 chars]
Continuous glucose monitors (CGMs) are becoming a wellness hacking and MAHA obsession. Experts weigh in on how much blood sugar fluctuations matter if you don't have diabetes or prediabetes.
Youve seen the patch on pro runners arms and heard the hype about tiny sensors feeding steady streams of glucose data to phones: Continuous Glucose Monitors (CGMs) are the latest obsession for big ph… [+8123 chars]
Invenio module for record classification.
Invenio module for record classification.
Features
Classifier automatically extracts keywords from fulltext documents. The
automatic assignment of keywords to textual documents has clear benefits
… [+6192 chars]
{ window.open(this.href, '_blank'); }, 200); return false;">Why was the Empire Wind vessel cancelled nearly complete? { window.open(this.href, '_blank'); }, 200); return false;">How will Nvidia… [+826 chars]
In 2020, Hinge introduced a controversial rose feature. Some women have learned how to free hot guys from ‘rose jail’ and get first dates.
The rules came from Megan, a friend of a friend who lives in Los Angeles and had recently done the impossible: Shed found a boyfriend on Hinge. Finding a boyfriend is the ostensible point of dating a… [+12835 chars]
'EastEnders' star Alice Haig reveals Vicki Fowler's fate after the shocking, violent attack by her stepson Joel Marshall. Read her emotional plea to parents.
Trigger Warning: This article discusses the plot of a fictional television programme, EastEnders, which includes graphic references to domestic violence, physical assault, misogyny, and a character b… [+4536 chars]
With AI capabilities and 87+ browser-based apps per organization, browsers have evolved into OSes that demand enterprise-grade security and management strategies.
From an application perspective, web browsers have become a sort of OS within an OS. With the introduction of agentic AI capabilities within the browser (just look at what Perplexity, Opera and, to s… [+4338 chars]